CMMC for Construction Project Management: Everything Federal Contractors Need to Know
In this article:
- What does CMMC mean for Federal Contractors?
- Background CMMC Levels for Construction Project Management
- Critical Dates and Deadlines
- Glossary of CMMC Terms More Trusted Resources
What is CMMC?

The Cybersecurity Maturity Model Certification (CMMC) is a framework introduced by the Department of Defense (DoD) to ensure contractors and subcontractors meet specific cybersecurity standards.
Its goal is to safeguard sensitive unclassified information, particularly Controlled Unclassified Information (CUI), from cyber threats.
For construction contractors, CMMC compliance is required to secure DoD contracts.
It is necessary to maintain a competitive edge in the government marketplace.
Background of CMMC
In 2020, the DoD introduced the original CMMC framework to strengthen cybersecurity across the Defense Industrial Base (DIB)—a network of organizations and facilities that provide the U.S. government with defense-related products and services.
The CMMC framework was built on existing requirements—most notably DFARS 252.204-7012—that requires contractors to protect CUI using NIST SP 800-171 standards.

In the past, contractors self-attested to compliance. But with rising cyber threats and inconsistent security practices, the DoD launched CMMC as a formal certification model, with independent assessments to validate security readiness.
For construction contractors working on DoD projects, CMMC ensures that sensitive facility and infrastructure data is protected—and that your firm stays eligible to win future contracts.
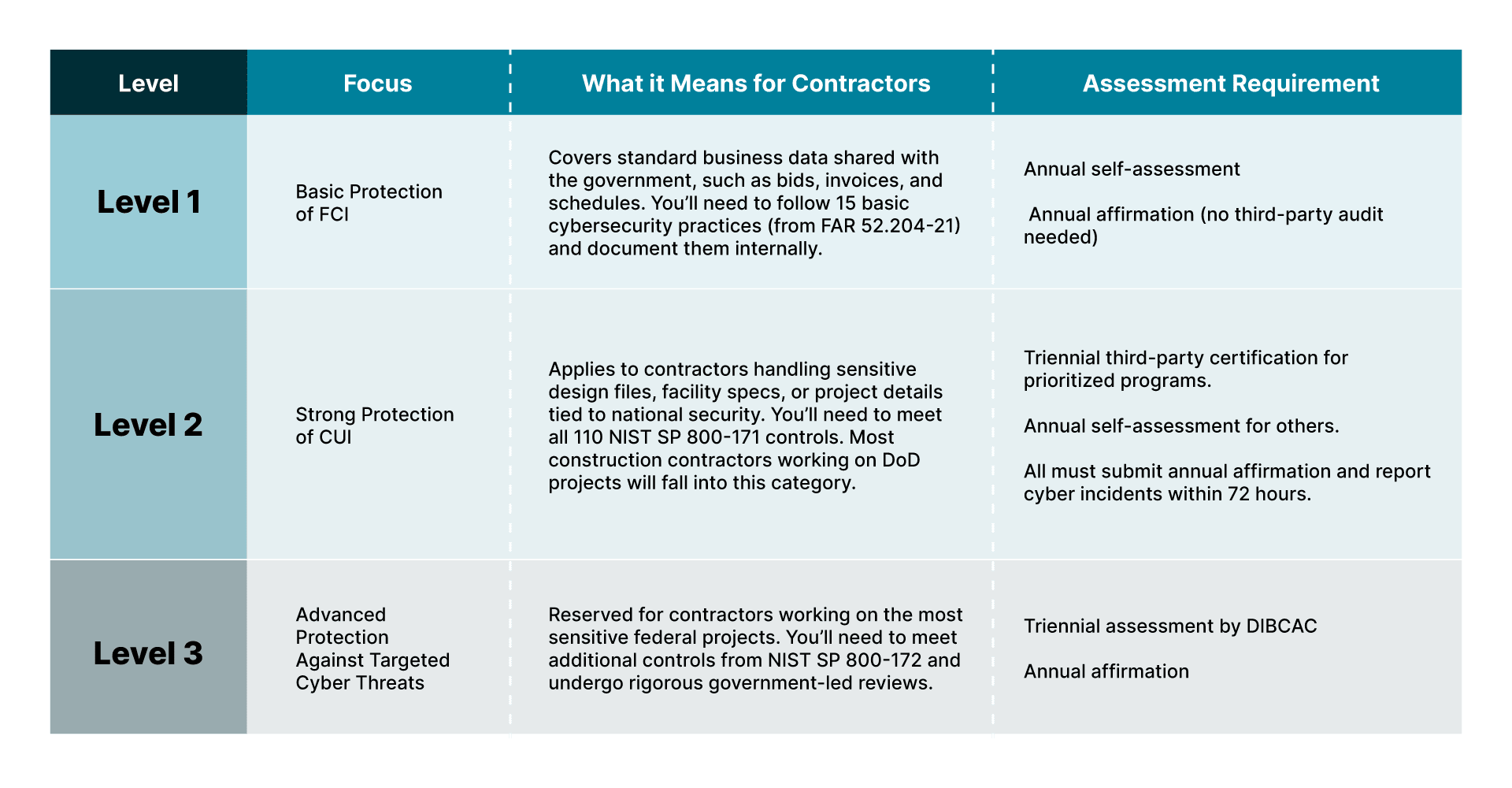
What are the CMMC Levels and Which Level do DoD Construction Contractors Need?
CMMC defines three certification levels, each with progressively stricter cybersecurity requirements for contractors handling sensitive unclassified DoD information, based on the data’s type and sensitivity.
Assessments, adjusted per level, allow the DoD to verify implementation. The program also explains how to ensure these safeguards are applied to information shared with subcontractors.
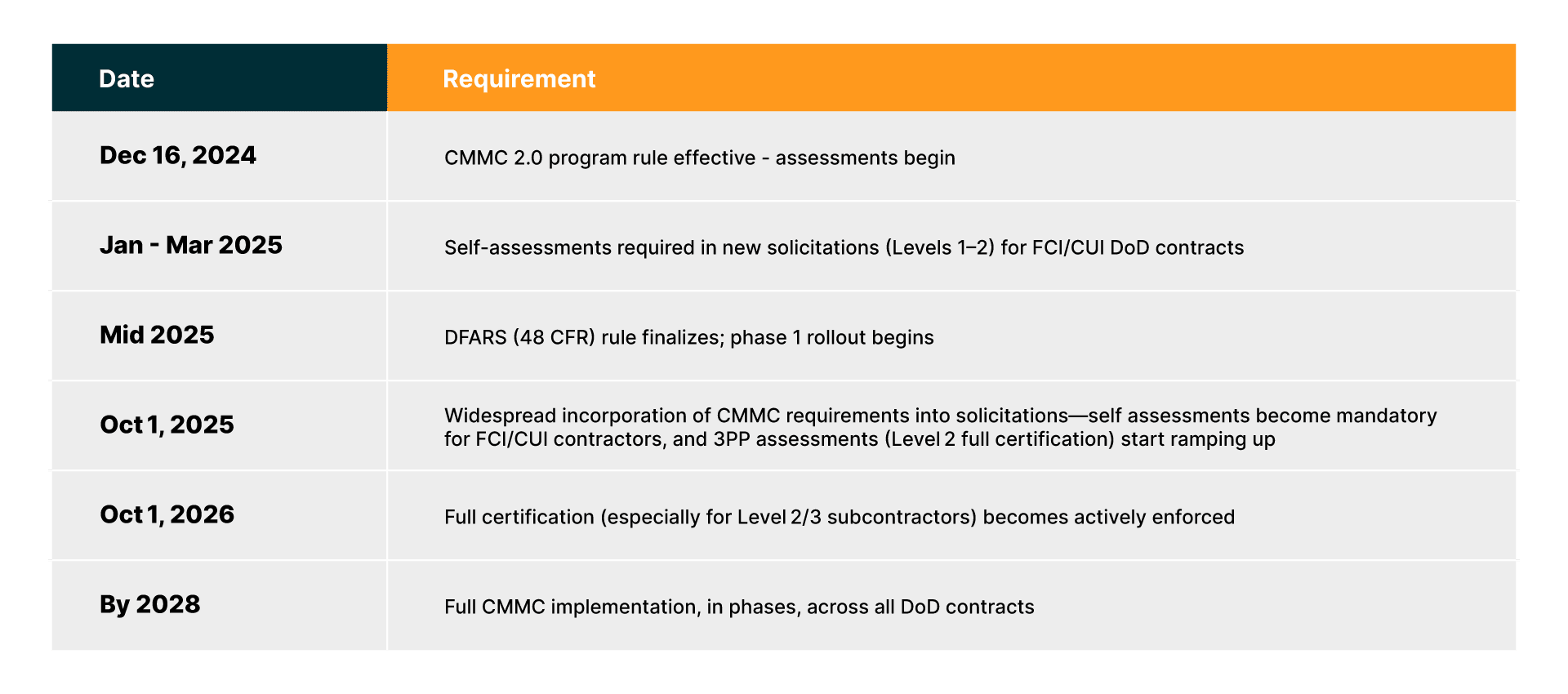
Critical Dates and Deadlines
How long does CMMC certification take? Good question – if everything is lined up and ready to go, it takes about 12 months.
Here are critical CMMC dates and deadlines:
So, what should you do now?
-
Don’t wait: With self-assessments now required and certification assessments ongoing, start preparing for or initiating an assessment immediately.
-
Establish a SPRS profile and POA&M plan: If gaps exist in your NIST SP-800171 compliance, track them with a Plan of Action & Milestones. Remediation must be completed within 180 days of a Conditional status.
-
For Level 2, get assessment going now: If handling CUI and aiming for CMMC Level-2, schedule your C3PAO (or DIBCAC for Level-3) now to secure your place in the pipeline before Q4-2025 demand peaks.
Glossary of CMMC Terms 
Anyone who has worked with the federal government knows that anything and everything has an abbreviation! Here’s your cheat sheet for fed-speak.
C3PAO: CMMC Third-Party Assessment Organization - The certified entity that evaluates and verifies a company’s compliance with CMMC requirements, ensuring eligibility to handle DoD projects.
CMMC: Cybersecurity Maturity Model Certification - Governs the cybersecurity requirements you must meet if handling DoD data.
CUI: Controlled Unclassified Information - Sensitive information subject to heightened security measures, including drawings, specifications, RFPs, and contracts; often requires CMMC Level 2 (or higher).
DBCAC: Defense Industrial-Based Cyber Assessment Center - A division of the DCMA that conducts cybersecurity assessments for high-level CMMC certifications (e.g., Level 3). Construction contractors on sensitive DoD projects may be evaluated by DIBCAC.
DCMA: Defense Contract Management Agency - Oversees contractor compliance with DoD requirements, including cybersecurity. Construction firms may interact with DCMA for contract audits or performance monitoring.
DFARS: Defense Federal Acquisition Regulation Supplement - Governs DoD contracts and includes clauses mandating cybersecurity (e.g., DFARS 252.204-7012).
DIB: Defense Industrial Base - Encompasses companies that provide goods, services, and support to the DoD. In construction, this can include general contractors building new military facilities and engineering firms maintaining or upgrading base infrastructure.
FAR: Federal Acquisition Regulation - The main rulebook for federal procurement. FAR clauses often mandate cybersecurity controls in construction contracts involving DoD work.
FCI: Federal Contract Information - Non-public data related to a federal contract; requires at least CMMC Level 1.
FedRAMP: Federal Risk and Authorization Management Program - Requires cloud service providers handling DoD data, such as Kahua, to meet FedRAMP Moderate (or equivalent) security standards.
NIST: National Institute of Standards and Technology - Creates guidelines (like NIST SP 800-171) that form the basis for meeting DoD cybersecurity rules. Construction companies with CUI must map their cybersecurity controls to these NIST requirements for meeting DFARS and CMMC obligations.
OSA: Organization Seeking Assessment - Any contractor pursuing CMMC certification. In construction, this typically refers to the general contractor or primary firm managing the CMMC process.
PMIS: Project Management Information System - Typically cloud based (like Kahua), a system that centralizes and secures project documentation, schedules, and communications in real time, supporting efficient collaboration and compliance with cybersecurity obligations.
PMO: Program Management Office (as in the CMMC PMO) - The DoD office responsible for managing the CMMC program, including timelines, requirements, and updates relevant to federal contractors.
POA&M or POAM: Plan of Actions and Milestones - A formal plan to fix security gaps identified during CMMC assessments. Must be resolved within deadlines to maintain compliance eligibility.
SP: Special Publication (used in NIST SP references) - An NIST-issued document that outlines technical security standards, like SP 800171. These form the foundation of CMMC requirements for handling sensitive project data.
SPRS: Supplier Performance Risk System - A DoD portal where contractors upload self-assessment scores for NIST SP 800-171. Required to bid on contracts involving FCI or CUI.
Trusted CMMC Resources
Looking for more guidance on CMMC requirements, timelines, and best practices?
The following trusted resources—maintained by U.S. government agencies and official CMMC partners—offer up-to-date information, tools, and policy references to help contractors navigate compliance with confidence.
-
DoD CIO: CMMC Program Overview
Authoritative DoD site explaining the purpose, structure, and rollout of the CMMC program.
-
Federal Register: CMMC Final Rule (32 CFR Part 170)
Official publication of the CMMC 2.0 final rule—effective December 16, 2024—with detailed regulatory requirements for Levels 1–3.
-
NIST SP-800171 (Rev.-3): Protecting CUI
The latest version of the NIST framework outlining security controls for protecting CUI—required for CMMC Level 2 compliance.
-
NIST SP 800-172: Enhanced Security for Critical Programs
Additional controls required for organizations seeking CMMC Level 3.
-
Cyber AB (Accreditation Body)
The official accreditation body for CMMC—includes directories of authorized assessors and training providers.
-
DCSA CUI Resources
Government-developed tools and guidance for identifying, marking, and managing CUI.
-
Project Spectrum
Free DoD-backed tools, training, and readiness assessments for small to mid-sized contractors.
-
DFARS Clause-252.2047012: Safeguarding Covered Defense Information & Cyber Incident Reporting
The DFARS clause that requires contractors to protect Covered Defense Information (like FCI and CUI) and to report cyber incidents to the DoD. Found in Subpart-204.73 and enforced across relevant DoD contracts.
Kahua's PMIS platform is FedRAMP certified and CMMC compliant.
If you're ready to start your CMMC certification process, talk to us today. We've been there!


